.Ghost.
Beginner 2.0
saya tau udah lama, cuma ga ngerti cara installnya..
Let's Enscrypt juga setahu saya program yang di dukung om Zuck.
Coba ikutin dokumentasi nya aja : https://letsencrypt.org/howitworks/
Kalau ini langkah-langkah saya ketika installasi dan konfigurasi di VPS Centos 7 saya:
Note:
- CentOS 7 64 bit minimal installation
- Service yang terinstall cm ada apache
- Konfigurasinya di lakukan di konfigurasi default apache dan home direktori nya
Pastikan server CentOS sudah mempunyai git dan repositori epel. Kalau belum install terlebih dahulu:
# yum install git
# yum install epel-release
# yum install mod_ssl
Download file letsencrypt:
# git clone https://github.com/letsencrypt/letsencrypt[/code]
Installasi letsencrypt:
# cd letsencrypt
# ./letsencrypt-auto --help
Setelah selesai, disini saya akan melakukan installasi sertifikat untuk domain enzu02.linboxs.net menggunakan command berikut:
]# ./letsencrypt-auto certonly --webroot -w /var/www/html -d enzu02.linboxs.net
Nanti akan muncul tampilan seperti berikut kemudian masukkan alamat email kita untuk kebutuhan recovery letsencrypt:
Tekan Enter untuk melanjutkan proses nya
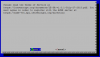
Setelah proses selesai akan muncul notifikasi seperti berikut:
IMPORTANT NOTES:
- If you lose your account credentials, you can recover through
e-mails sent to [email protected].
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/enzu02.linboxs.net/fullchain.pem. Your cert
will expire on 2016-04-01. To obtain a new version of the
certificate in the future, simply run Let's Encrypt again.
- Your account credentials have been saved in your Let's Encrypt
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Let's
Encrypt so making regular backups of this folder is ideal.
- If you like Let's Encrypt, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
File sertifikat akan tersimpan di :
/etc/letsencrypt/live/enzu02.linboxs.net/
Edit file ssl.conf:
# vim /etc/httpd/conf.d/ssl.conf
Rubah letak file SSLCertificateFile, SSLCertificateKeyFile dan SSLCertificateChainFile seperti berikut:
SSLCertificateFile /etc/letsencrypt/live/enzu02.linboxs.net/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/enzu02.linboxs.net/privkey.pem
SSLCertificateChainFile /etc/letsencrypt/live/enzu02.linboxs.net/chain.pem
Setelah itu restart service apache nya:
# systemctl restart httpd
Cek di browser apakah SSL sudah terdeteksi di browser seperti gambar berikut:
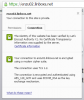
Kalau hasil di browser sudah menampilkan seperti gambar di atas artinya domain kita sudah terenkripsi menggunakan SSL Letsencrypt.
Meski gratis SSL Letsencrypt ini hanya valid selama 3 bulan, kalau sudah habis maka kita harus renewal sertifikat lagi. Mudah2an bermanfaat.


